In this blog entry it is explained what confidential computing is and how it works. Have a look at this https://www.opensourcerers.org/2023/12/11/confidentiality-in-a-crazy-world/ to find out more.
We now know how it works. But now we are looking into the use cases of Confidential Computing I have seen so far.
The basic principle Confidential Computing revolves around is trust. So where is it where data or business logic need extra protection against a possible intruder? The following 5 use case categories can currently be seen.
Partner interaction
In this use case several partners interact or want to provide a collaborative service. To be able to do so they all need to combine different business logic elements and the corresponding data. Neither trusts the other to host the environment or has the capacity to do so. That is why they choose to use a public cloud infrastructure. In most of those cases the access to the data and the business logic needs to be restricted towards the cloud provider and / or each other. Confidential Computing can be used to reduce the possible interaction with the data and audit its delivery for the purpose of contractual evidence gathering. A central confidential container is used. Each of the components uses its attestation service to retrieve the necessary key to decrypt their private business logic and its data for the interaction. Also each of the participants signs the central code which is executed in the Trusted Execution Environment to make sure there are no backdoors implemented in that code and all are getting the same result from the execution inside the confidential environment.
Secure Cloud Burst
Here a company is looking to enhance their on premise infrastructure with compute resources in the cloud. Those services need to be secured so for example no government agency through the public cloud provider can access that information. The advantages of a public cloud can be used to dynamically add compute resources to the execution of an on premise application. This can range from offloading specific services which take advantage of infrastructure components like GPUs into the public cloud to establishing a whole application in that environment to make it independent from the on premise infrastructure. Here a confidential container or even a confidential clusters can be used to enable such a cloud burst scenario. As an example of such a use case have a look at this blog entry ( https://www.redhat.com/en/blog/confidential-containers-fsi-public-cloud ) were cloud provided GPUs are used to execute an AI model.
IP Protection / Integrity Protection
In this case there is a service provider who sells its services to a customer which means they have to add application logic and data to the in house environment of that customer. This means that the customer could get access to this sensible and valuable IP. The service provider wants to restrict the access to the business logic and restrict the ability to change code for reasons of liability. Therefor confidential computing or more specific a Confidential Container can be used. In that case the customer provides the environment to run the Confidential Container or if the environment needed is more complicated a Confidential Cluster. The service provider gets the rights to start it on the customers environment and supplies their own attestation service and deploy the business logic and the data as needed. Components in the customers environment can then interact with this suppliers business logic in a secure way.
Edge use cases
There are different scenarios for edge use cases. It all depends on where there is a confidential environment available. The further to the edge we are looking the more scarce the CPUs that support Confidential Computing are available. In march ARM announced to further add confidential services to their architecture for edge deployment. ( https://community.arm.com/arm-community-blogs/b/architectures-and-processors-blog/posts/unlocking-the-power-of-data-with-arm-cca ). Looking more into near edge deployments other hardware providers are stepping in with their implementations. Here we can see use cases which focus more on the data privacy area like health data or personal location based services. To protect that data the closer to the edge a confidential environment is used the better. But at least at the second tier ( Aggregation of personal information at the server level ) is where Confidential Computing can help. In this tier the data is collected, then aggregated and send in an anonymized way to the tariff calculation to the on premise environment. The aggregation tier is located in the public cloud to take advantage of the flexible and consumption based compute power. Also as described in the FSI use case optionally the usage of GPUs would be possible in that tier.
Total Tenant Isolation
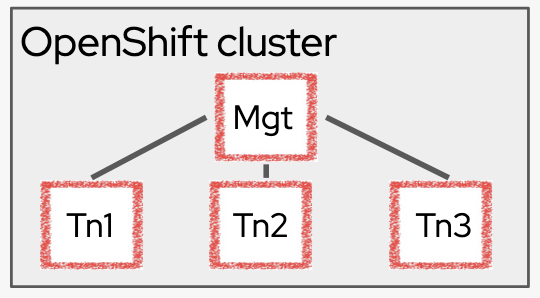
For the high security focused industries we have seen in many different Regions the use case of a total separation of tenants in one OpenShift installation with the goal of a bare metal installation. So in this scenario not only the networking separation is called for each tenant but also separation of the management nodes from the rest and the separation of the worker nodes from each other. All of those could be configured with different attestation services and with that different Key Management Services / repositories if needed. Confidential Computing isolates each execution environment from all of the others. Here again Confidential container or Confidential VMs can be used.
As we are at the beginning of the journey towards a confidential world most of the scenarios have not been implemented yet. These need to be prioritized and for that we need customers to walk on that road together with us. Or you think of a use case which is not covered here. Let us have a discussion on the use cases you see or their implementations.

