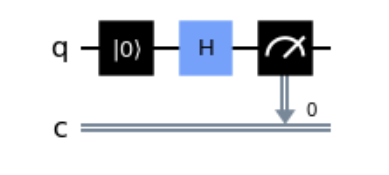
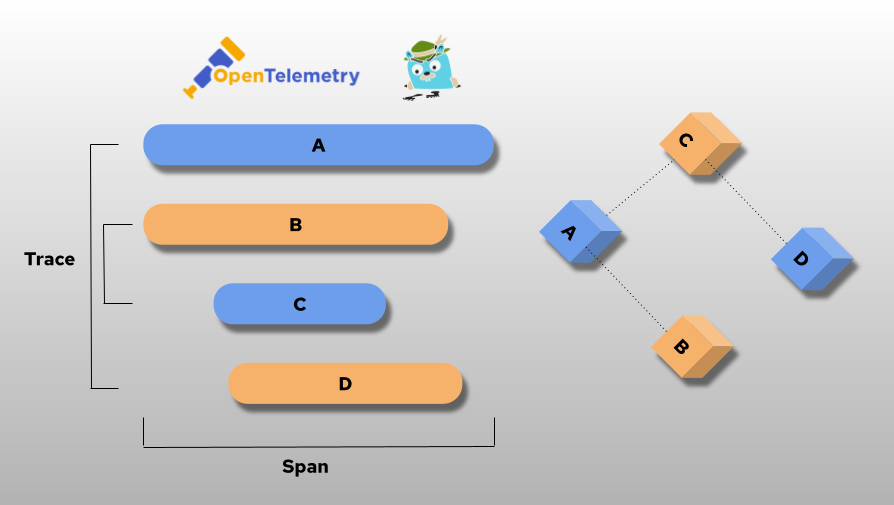
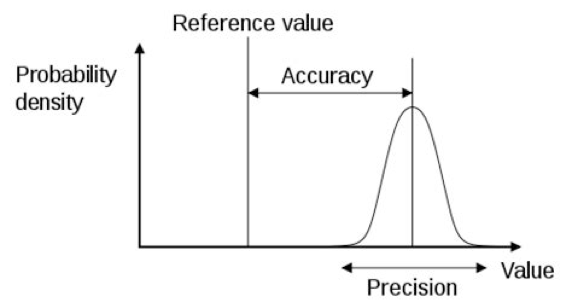
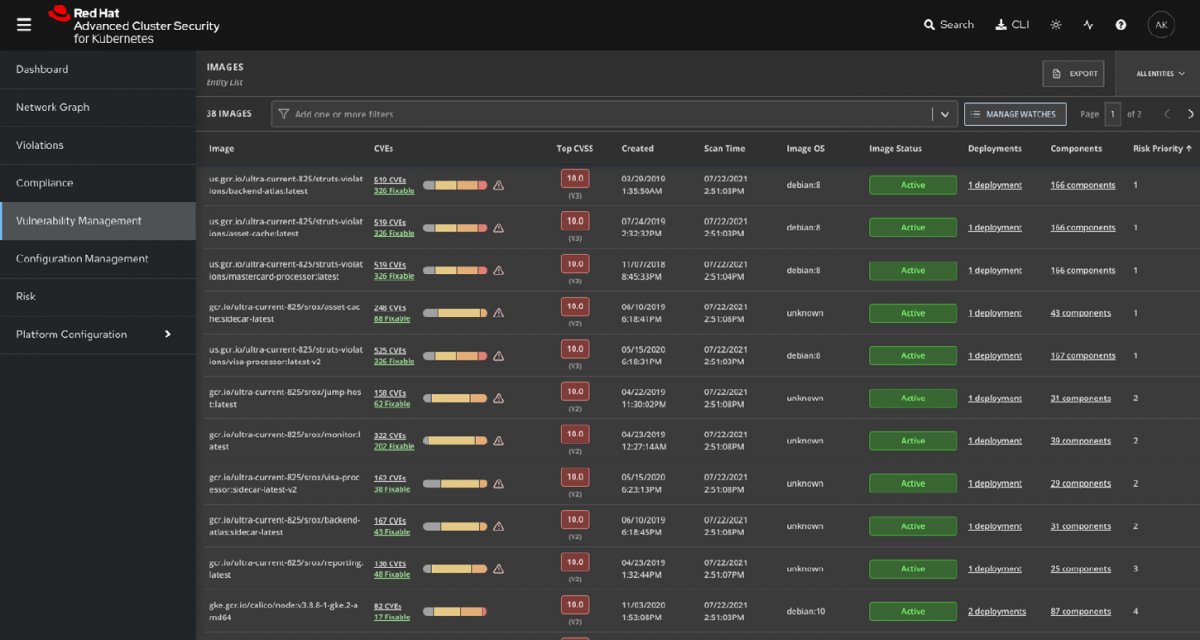
Introduction Customer requirements are constantly changing and the digital transformation of any company requires not only support for cultural aspects in the collaboration between departments and colleagues, but also the adaptation of processes, modernisation of programmes and the management of company-related data. In my article “How to create a data pipeline for Next Generation Sequencing”, […]