This article shows how MuleSoft’s Runtime Fabric (RTF) deployed to Red Hat OpenShift delivers a modern containerized API solution.


This article shows how MuleSoft’s Runtime Fabric (RTF) deployed to Red Hat OpenShift delivers a modern containerized API solution.
Introduction As a Solution Architect for Red Hat’s ecosystem, I talk to many independent software vendors (ISVs) about modernizing their applications to enable hybrid cloud and edge strategies. Linux, containers, Kubernetes and micro-services architecture are a default choice nowadays in many new application development projects. But sometimes you can not get rid of some dependencies […]
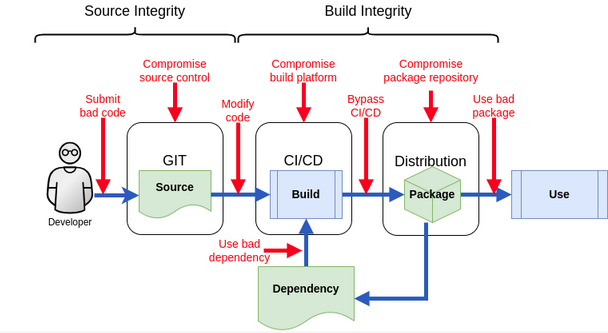
What is Software Supply Chain Security ? In this day and age most of us are looking for trust and security. This is also true for our IT infrastructure as challenges from the outside grow more and more dangerous to the continuation of undisturbed business. Attacks on the IT infrastructure of companies not only rise […]

As a computer scientist, I think the best thing about our job is clearly the need to keep up with the latest technological achievements. Depending on the specific area you work in, you can actually always be sure that the solutions to challenges are constantly changing. Kubernetes is no different in that regard. Let’s find […]

San Francisco, June 9-10, 2014. In the halls of the Marriott Marquis hotel, the first DockerCon is held. “Containers everywhere!” is printed on the back of event T-shirts. The first big news of DockerCon is the launch of Docker 1.0, but there is much more to come. It is the beginning of what is later […]

Target group: If you are a solution architect or consultant looking for some references of distributed data messaging solutions at a high level, this is an article for you. As well, if you are experiencing significant growth at your company and your messaging system is struggling to handle the volume of traffic, you experience frequent […]

Overview How can we secure the integrity of our Software Supply Chains and have confidence that our software has not been tampered with and can be traced to its source? Which are the main parts of the software supply chain security? Before explaining how to secure the Software Supply Chain, we need first to understand […]

In Part II of our 4-part blog series “You’ve written a Kubernetes-native Application? Here is how OpenShift helps you to run, develop, build and deliver it”, we will focus on the aspect of developing our application with and directly on OpenShift. In Part I, we’ve introduced our sample application “the Local News Application”, and showed […]
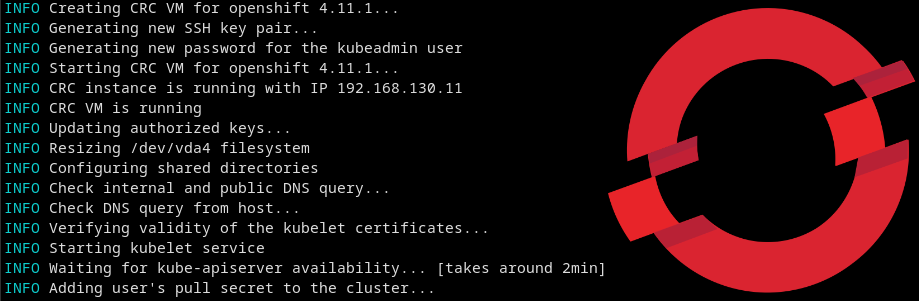
Are you a developer or just a curious individual who wants to dip their toes in the Cloud, but are not sure whether to go for OpenShift Local or Single Node OpenShift? You’ve come to the right place. In this article, I will explore the differences and similarities between these two variants of OpenShift, so […]

Summary This article describes the installation of Red Hat Advanced Cluster Security (RHACS) using the Operator. It also covers the integration of Tekton Pipelines for the deployment of two different containers and the configuration of a Slack notification. A special feature here is that the installation and configuration is largely automated by scripts and can […]