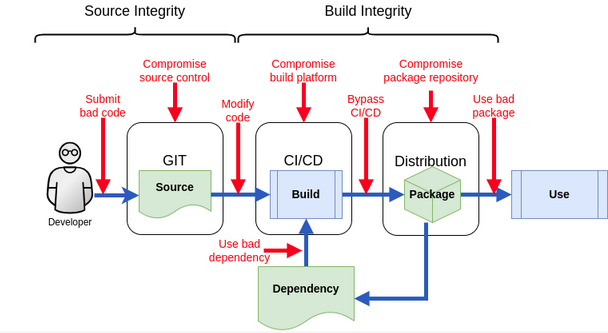
A Guide to Seamless Connectivity in OpenShift and OKD In today’s rapidly evolving technological landscape, the integration of complex architectures into our systems is becoming more prevalent than ever. One of these challenges is to consolidate a multi-cloud architecture into a true hybrid cloud one. In this blog post we will delve into the motivations, solutions, and considerations […]