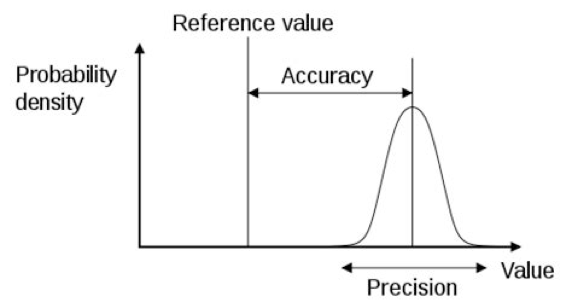
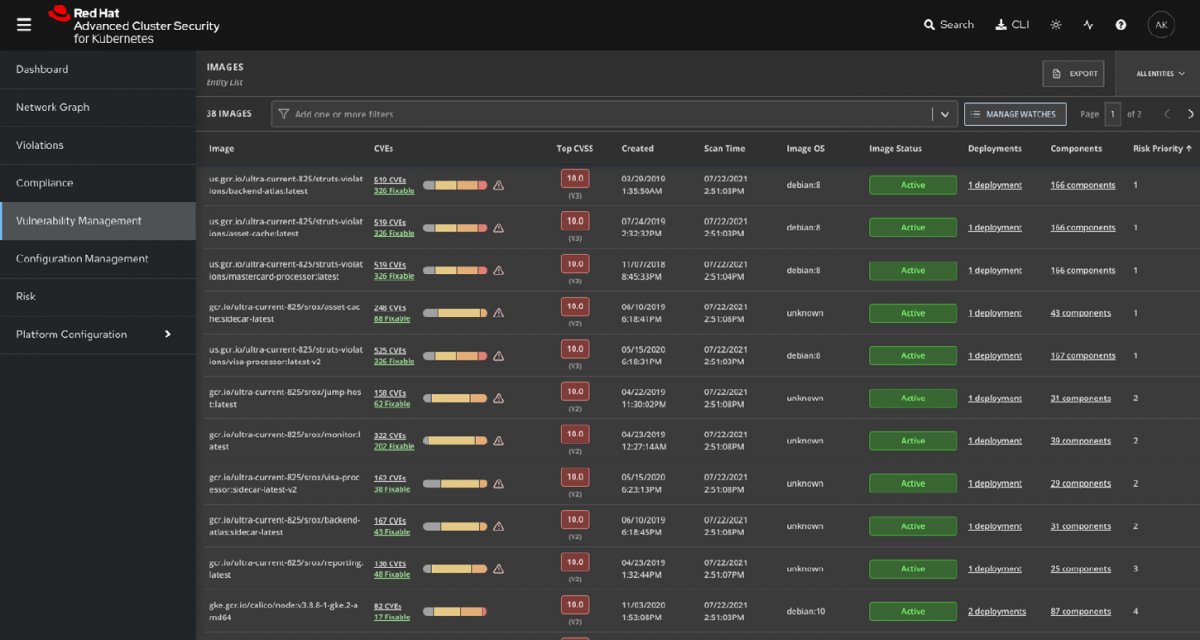
Summary This article describes the installation of Red Hat Advanced Cluster Security (RHACS) using the Operator. It also covers the integration of Tekton Pipelines for the deployment of two different containers and the configuration of a Slack notification. A special feature here is that the installation and configuration is largely automated by scripts and can […]