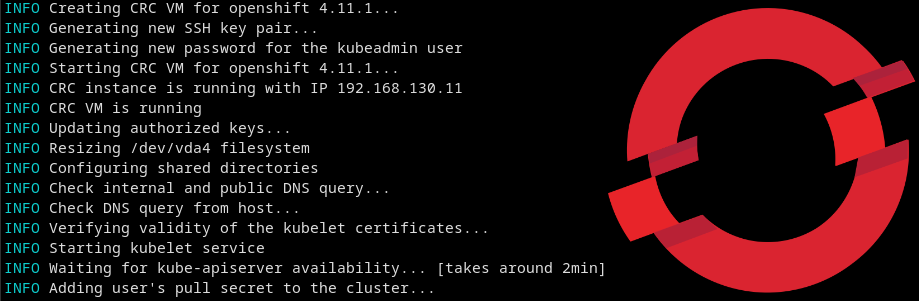
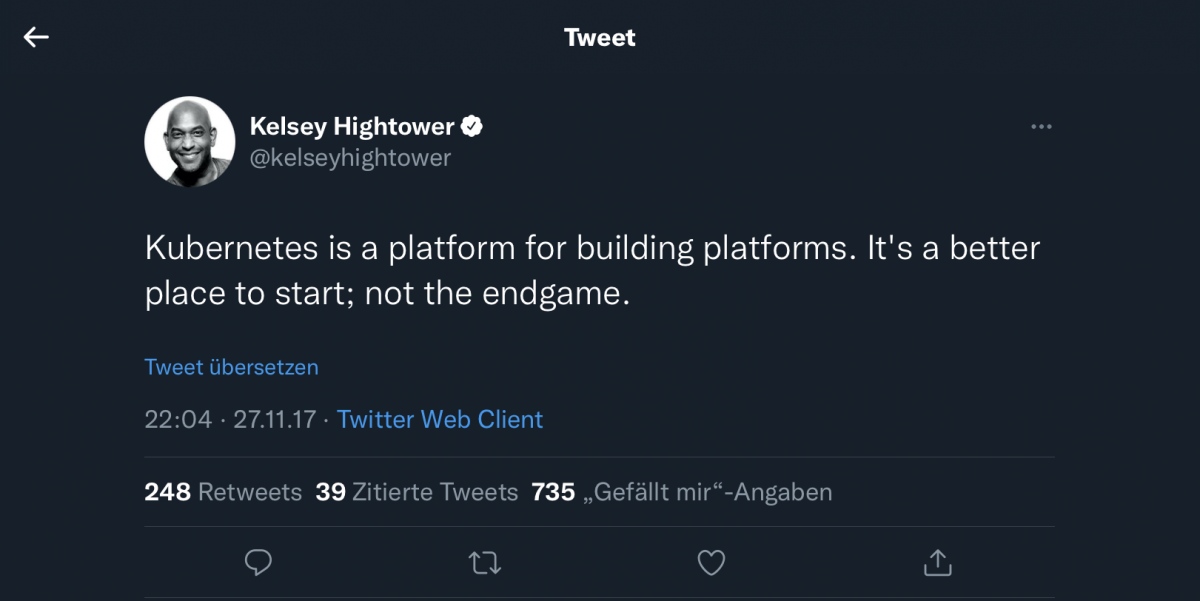
San Francisco, June 9-10, 2014. In the halls of the Marriott Marquis hotel, the first DockerCon is held. “Containers everywhere!” is printed on the back of event T-shirts. The first big news of DockerCon is the launch of Docker 1.0, but there is much more to come. It is the beginning of what is later […]